Microsoft Radius Server Mac Filtering Cisco Wlan Controller
Posted By admin On 09.04.20- Linksys Mac Filtering
- Microsoft Radius Server Mac Filtering Cisco Wlan Controller Free
- Microsoft Radius Server Mac Filtering Cisco Wlan Controller Windows 10
- Where Is Mac Filtering
- Microsoft Radius Server Mac Filtering Cisco Wlan Controller Download
Linksys Mac Filtering
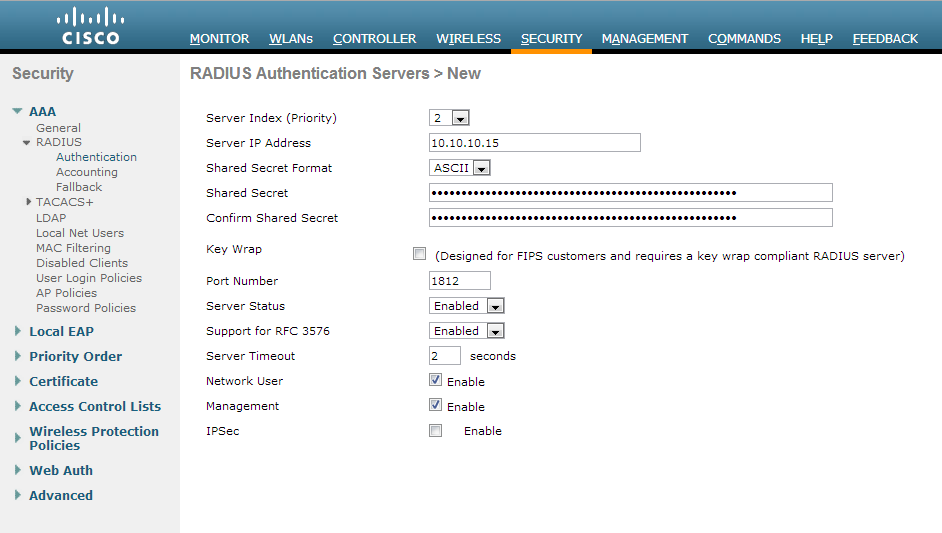
Mar 29, 2011 Use the config macfilter add command in order to create a MAC filter entry on the Cisco Wireless LAN controller. Use this command in order to add a client locally to a wireless LAN on the Cisco Wireless LAN controller. This filter bypasses the RADIUS authentication process. Cisco WLC With FreeRADIUS configured, it is time to head to WLC and configure it. Starting with adding the radius server under Security - AAA - Radius - Authentication. In the shared secret, make sure to enter the same as you did in the entry in the users file above. Then it is time to create the WLAN. Ah ok:) So yes, you should be able to perform your user or machine based authentication against AD and also check the MAC address against the database of your Radius server. I have personally done this with both ISE and ACS. In the WLC you will set your regular 802.1x settings and also check 'mac filtering.' Tutorial: 802.1X Authentication via WiFi – Active Directory Network Policy Server Cisco WLAN Group Policy Here is how to implement 802.1X authentication in a Windows Server 2008 R2 domain environment using Protected-EAP authentication. I have designed the tutorial to be worked on in the specific order to prevent downtime if deployed during the day. 77 thoughts on “ Tutorial: 802.1X Authentication via WiFi – Active Directory + Network Policy Server + Cisco WLAN + Group Policy ” Alejandro July 26, 2013 at 10:08 am. Hi, i follow al the guide, but when i try to autenticate via wireless i cant. I enable the debug in the WLC and i have this error.
Applies To: Windows Server 2012
This document provides introductory information about Institute of Electrical and Electronics Engineers (IEEE) 802.1X authenticated access for IEEE 802.11 wireless access. Links to resources with information about technologies that are closely related to 802.1X authenticated wireless access, or otherwise relevant to wireless access are also provided.
Note
In addition to this topic, the following 802.1X Authenticated Wireless Access documentation for Windows Server 2012 is also available.What's New in 802.1X Authenticated Wireless AccessImprovements to Certificate-based AuthenticationWireless LAN Service OverviewManaging the Wireless Network (IEEE 802.11) PoliciesCore Network Companion Guide: Deploying Password-based 802.1X Authenticated Wireless AccessNew Wireless Connection Processes
Did you mean…
Netsh Commands for Wireless Local Area Network (WLAN) in the Windows Server 2008 R2 and Windows Server 2008 technical library on TechNet.
802.1X Authenticated Wireless Access in the Windows Server 2008 R2 and Windows Server 2008 technical library on TechNet.
Feature description
IEEE 802.1X authentication provides an additional security barrier for your intranet that you can use to prevent guest, rogue, or unmanaged computers that cannot perform a successful authentication from connecting to your intranet.
For the same reason that administrators deploy IEEE 802.1X authentication for IEEE 802.3 wired networks—enhanced security—network administrators want to implement the IEEE 802.1X standard to help protect their wireless network connections. Just as an authenticated wired client must submit a set of credentials to be validated before being allowed to send frames over the wired Ethernet intranet, an IEEE 802.1X wireless client must also perform authentication prior to being able to send traffic over its wireless access point (AP) port, and over the network.
Important terminology and technology overviews
Following are overviews that will help you to understand the various technologies that are required to deploy 802.1X authenticated wireless access.
Note
In this document, 802.1X authenticated wireless access is referred to as WiFi access.
IEEE 802.1X
Microsoft Radius Server Mac Filtering Cisco Wlan Controller Free
The IEEE 802.1X standard defines the port-based network access control that is used to provide authenticated WiFi access to corporate networks. This port-based network access control uses the physical characteristics of the 802.1X capable wireless APs infrastructure to authenticate devices attached to a LAN port. Access to the port can be denied if the authentication process fails. Although this standard was first designed for wired Ethernet networks, it has also been adapted for use on 802.11 wireless LANs.
IEEE 802.1X-capable wired Ethernet switches
To deploy 802.1X wireless access you must install and configure one or more 802.1X-capable wireless APs on your network. The wireless APs must be compatible with the Remote Authentication Dial-In User Service (RADIUS) protocol.
When 802.1X and RADIUS-compliant wireless APs are deployed in a RADIUS infrastructure, with a RADIUS server such as an NPS server, they are called RADIUS clients.
IEEE 802.11 wireless
IEEE 802.11 is a collection of standards that defines the Layer-1 (physical layer) and Layer-2 (data-link layer media access control (MAC)) of WiFi access.
Network Policy Server
Network Policy Server (NPS) lets you centrally configure and manage network policies by using the following three components: RADIUS server, RADIUS proxy, and Network Access Protection (NAP) policy server. NPS is required to deploy 802.1X wireless access.
Server certificates
WiFi access deployment requires server certificates for each NPS server that performs 802.1X authentication.
A server certificate is a digital document that is commonly used for authentication and to help secure information on open networks. A certificate securely binds a public key to the entity that holds the corresponding private key. Certificates are digitally signed by the issuing certification authority (CA), and they can be issued for a user, a computer, or a service.
A CA is an entity responsible for establishing and vouching for the authenticity of public keys that belong to subjects (usually users or computers) or other CAs. Activities of a CA can include binding public keys to distinguished names through signed certificates, managing certificate serial numbers, and revoking certificates.
Active Directory Certificate Services (AD CS) is a Windows Server 2012 server role that issues certificates as a network CA. An AD CS certificate infrastructure, also called a public key infrastructure (PKI), provides customizable services for issuing and managing certificates for the enterprise.
EAP
Extensible Authentication Protocol (EAP) extends Point-to-Point Protocol (PPP) by enabling additional authentication methods that use credential and information exchanges of arbitrary lengths. With EAP authentication, both the network access client and the authenticator (such as an NPS server) must support the same EAP type for successful authentication to occur.
New and changed functionality
In Windows Server 2012, WiFi access includes only minimal changes to the wired access solution provided in Windows Server 2008 R2. That change is summarized as follows:
Feature/functionality | Previous operating system | New operating system |
|---|---|---|
The addition of EAP-Tunneled Transport Layer Security (EAP-TTLS) to the list of network authentication methods that are included by default | Not included | Included by default |
See also
Following are additional resources that pertain to 802.1X authenticated wireless access.
Microsoft Radius Server Mac Filtering Cisco Wlan Controller Windows 10
Content type | References |
|---|---|
Product evaluation | Connecting to Wireless Networks with Windows 7 The Cable Guy - July 2010 |
Planning Microsoft project management for mac os. | Windows Server 2008 802.1X Authenticated Wireless Access Design Guide |
Deployment | Windows Server 2008 802.1X Authenticated Wireless Access Deployment Guide Windows Server 2012 Core Network Companion Guide: Deploying Password-based 802.1X Authenticated Wireless Access Windows Server 2008 R2 Core Network Companion Guide: Deploying Password-based 802.1X Authenticated Wireless Access |
Operations | Windows Server 2012 Managing the Wireless Network (IEEE 802.11) Policies extension of Group Policy Extensible Authentication Protocol (EAP) Settings for Network Access Windows Server 2012 Wireless LAN Service Overview Windows Server 2008 R2 Netsh Commands for Wireless Local Area Network (WLAN) |
Troubleshooting | Windows Server 2008 R2 Network Diagnostics Framework (NDF) and Network Tracing |
Security | Content not available |
Tools and settings | Windows Server 2012 Managing the Wireless Network (IEEE 802.11) Policies extension of Group Policy |
Community resources | Content not available |
Related technologies | Windows Server 2008 R2 802.1X Authenticated Wired Access Windows Server 2008 R2 Network Policy and Access Services |
Applies to: Windows Server (Semi-Annual Channel), Windows Server 2016
You can use this guide to deploy server certificates to your Remote Access and Network Policy Server (NPS) infrastructure servers.
This guide contains the following sections.
Digital server certificates
This guide provides instructions for using Active Directory Certificate Services (AD CS) to automatically enroll certificates to Remote Access and NPS infrastructure servers. AD CS allows you to build a public key infrastructure (PKI) and provide public key cryptography, digital certificates, and digital signature capabilities for your organization.
When you use digital server certificates for authentication between computers on your network, the certificates provide:
- Confidentiality through encryption.
- Integrity through digital signatures.
- Authentication by associating certificate keys with computer, user, or device accounts on a computer network.
Server types
By using this guide, you can deploy server certificates to the following types of servers.
- Servers that are running the Remote Access service, that are DirectAccess or standard virtual private network (VPN) servers, and that are members of the RAS and IAS Servers group.
- Servers that are running the Network Policy Server (NPS) service that are members of the RAS and IAS Servers group.
Advantages of certificate autoenrollment
Automatic enrollment of server certificates, also called autoenrollment, provides the following advantages.
- The AD CS certification authority (CA) automatically enrolls a server certificate to all of your NPS and Remote Access servers.
- All computers in the domain automatically receive your CA certificate, which is installed in the Trusted Root Certification Authorities store on every domain member computer. Because of this, all computers in the domain trust the certificates that are issued by your CA. This trust allows your authentication servers to prove their identities to each other and engage in secure communications.
- Other than refreshing Group Policy, the manual reconfiguration of every server is not required.
- Every server certificate includes both the Server Authentication purpose and the Client Authentication purpose in Enhanced Key Usage (EKU) extensions.
- Scalability. After deploying your Enterprise Root CA with this guide, you can expand your public key infrastructure (PKI) by adding Enterprise subordinate CAs.
- Manageability. You can manage AD CS by using the AD CS console or by using Windows PowerShell commands and scripts.
- Simplicity. You specify the servers that enroll server certificates by using Active Directory group accounts and group membership.
- When you deploy server certificates, the certificates are based on a template that you configure with the instructions in this guide. This means that you can customize different certificate templates for specific server types, or you can use the same template for all server certificates that you want to issue.
Prerequisites for using this guide
Where Is Mac Filtering
This guide provides instructions on how to deploy server certificates by using AD CS and the Web Server (IIS) server role in Windows Server 2016. Following are the prerequisites for performing the procedures in this guide.
You must deploy a core network using the Windows Server 2016 Core Network Guide, or you must already have the technologies provided in the Core Network Guide installed and functioning correctly on your network. These technologies include TCP/IP v4, DHCP, Active Directory Domain Services (AD DS), DNS, and NPS.
Note
The Windows Server 2016 Core Network Guide is available in the Windows Server 2016 Technical Library. For more information, see Core Network Guide.
You must read the planning section of this guide to ensure that you are prepared for this deployment before you perform the deployment.
You must perform the steps in this guide in the order in which they are presented. Do not jump ahead and deploy your CA without performing the steps that lead up to deploying the server, or your deployment will fail.
You must be prepared to deploy two new servers on your network - one server upon which you will install AD CS as an Enterprise Root CA, and one server upon which you will install Web Server (IIS) so that your CA can publish the certificate revocation list (CRL) to the Web server.
Note
You are prepared to assign a static IP address to the Web and AD CS servers that you deploy with this guide, as well as to name the computers according to your organization naming conventions. In addition, you must join the computers to your domain.
What this guide does not provide
This guide does not provide comprehensive instructions for designing and deploying a public key infrastructure (PKI) by using AD CS. It is recommended that you review AD CS documentation and PKI design documentation before deploying the technologies in this guide.
Technology overviews
Following are technology overviews for AD CS and Web Server (IIS).
Active Directory Certificate Services
AD CS in Windows Server 2016 provides customizable services for creating and managing the X.509 certificates that are used in software security systems that employ public key technologies. Organizations can use AD CS to enhance security by binding the identity of a person, device, or service to a corresponding public key. AD CS also includes features that allow you to manage certificate enrollment and revocation in a variety of scalable environments.
Microsoft Radius Server Mac Filtering Cisco Wlan Controller Download
For more information, see Active Directory Certificate Services Overview and Public Key Infrastructure Design Guidance.
Web Server (IIS)
The Web Server (IIS) role in Windows Server 2016 provides a secure, easy-to-manage, modular, and extensible platform for reliably hosting websites, services, and applications. With IIS, you can share information with users on the Internet, an intranet, or an extranet. IIS is a unified web platform that integrates IIS, ASP.NET, FTP services, PHP, and Windows Communication Foundation (WCF).
For more information, see Web Server (IIS) Overview.